What is Backup? Understanding how files are copied
What is backup? In this comprehensive guide, we will show you how to make a backup copy of the files on your computer Backing up your files is the process…

What is backup? In this comprehensive guide, we will show you how to make a backup copy of the files on your computer Backing up your files is the process…

It is crucial that you understand the risks related to identity theft, photo manipulation, and harassment generated by images displayed in the search engine; these risks can be…

Here are some tips that will help you save space in the cloud and back up files to iCloud such as photos, WhatsApp conversations, apps, and other files. As…
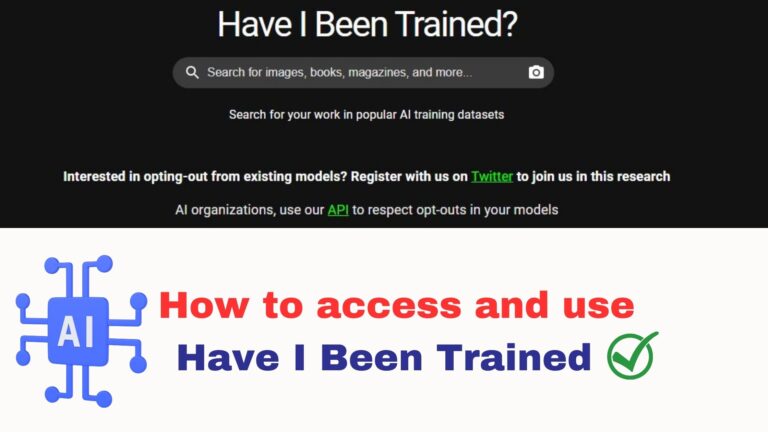
Learn how to access and use Have I Been Trained, a free platform that removes images from AI training databases The Have I Been Trained website lets you find…

Check out five options to see if a website’s reliability can be verified using a link checker platform, which can be a useful tool to maintain online security. It…

Using this platform, users can view sports competitions in an unofficial manner; however, it might pose a threat to their digital security; find out more about how it works…
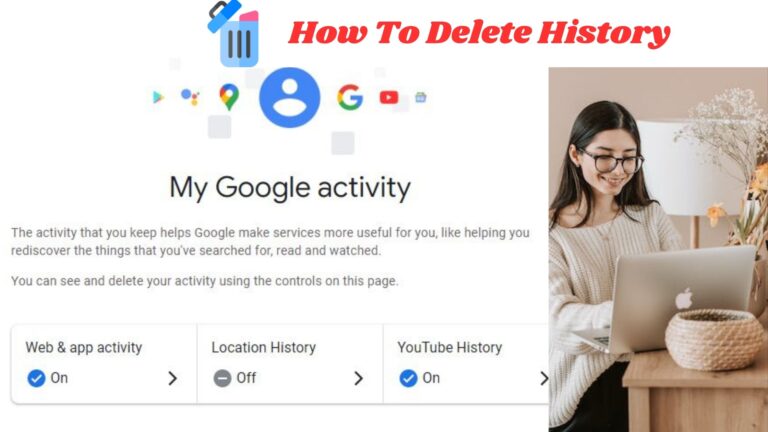
It is possible to view and delete your history on the “Google My Activity” page, as well as manage all of the data you have shared with the company’s…

Using phishing links to steal victim information is a common Internet scam; learn how to protect yourself and your computer There is no doubt that phishing links are a…
This is an example of a malicious program known as a Trojan horse, which masquerades itself as an ordinary program and is used to infect a computer system. Trojan…

Security holes can be exploited by cybercriminals to gain access to webcam and film users without their knowledge. Information on identifying potential attackers can be found here. A webcam…